IDS vs. IPS
المحاضر : المهندس أحمد سلطان
للمزيد من الكورسات المجانية إضغط هنا
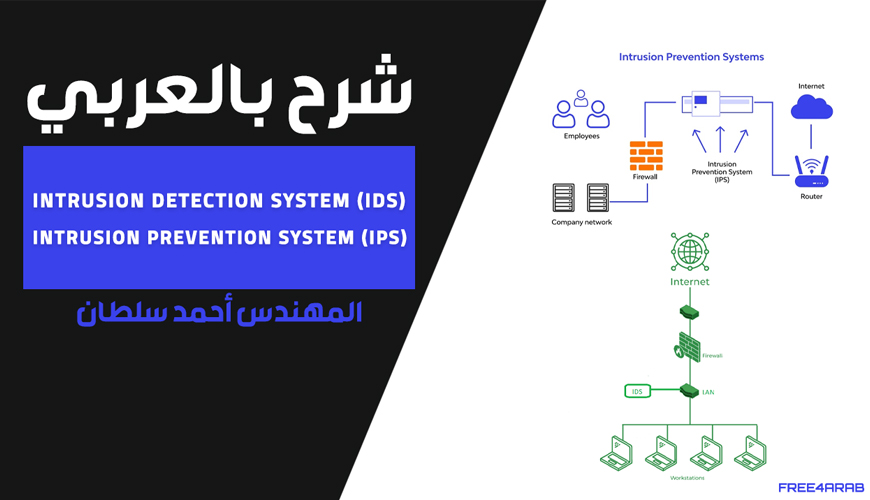
Intrusion Detection System (IDS)
Intrusion Prevention System (IPS)
IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) are both network security technologies designed to monitor and protect systems from malicious activities, but they operate in slightly different ways:
1. Intrusion Detection System (IDS):
- Purpose: Detects and alerts about potential security breaches, but does not actively block them.
- How It Works: IDS monitors network traffic or system activities for suspicious patterns or known attack signatures. When an intrusion is detected, it generates an alert, which is then investigated by a security team.
- Types of IDS:
- Network IDS (NIDS): Monitors network traffic for signs of intrusion.
- Host-based IDS (HIDS): Monitors activity on a specific device or host, such as a server or workstation.
- Example: If an IDS detects an unusual number of failed login attempts from a specific IP address, it generates an alert, but it doesn’t block the IP or stop the login attempts.
- Advantages:
- Passive monitoring (no interference with network traffic).
- Alerts security teams about potential threats.
- Disadvantages:
- Cannot actively block or mitigate attacks.
- Generates alerts that require manual investigation, which could delay response time.
2. Intrusion Prevention System (IPS):
- Purpose: Actively prevents potential intrusions by detecting and blocking malicious activities in real time.
- How It Works: IPS monitors network traffic for known attack signatures and suspicious behavior, similar to IDS, but unlike IDS, it can take immediate action to block or stop the attack. For example, it can drop malicious packets, block an IP address, or terminate a connection.
- Types of IPS:
- Network-based IPS (NIPS): Analyzes and blocks traffic on the network.
- Host-based IPS (HIPS): Works on individual hosts or endpoints to prevent attacks.
- Example: If an IPS detects an ongoing SQL injection attack, it will immediately block the malicious traffic and prevent the attack from reaching the server.
- Advantages:
- Real-time threat blocking.
- Provides an automated response to mitigate risks without waiting for human intervention.
- Disadvantages:
- Can sometimes block legitimate traffic if not properly configured.
- May introduce latency or performance degradation if not optimized.
Key Differences:
| Feature | IDS (Intrusion Detection System) | IPS (Intrusion Prevention System) |
|---|---|---|
| Primary Function | Detects and alerts on intrusions. | Detects and prevents intrusions. |
| Response to Threats | Generates alerts (passive). | Blocks or prevents attacks (active). |
| Network Impact | No impact on network traffic. | May impact network performance due to blocking actions. |
| Example of Action | Alerting the admin about a suspicious activity. | Blocking a malicious IP or packet. |
Combined Systems:
Many modern systems integrate both IDS and IPS functionalities, allowing for comprehensive detection and prevention. These are often referred to as IDPS (Intrusion Detection and Prevention Systems).
To summarize:
- IDS: Detects and alerts, no active defense.
- IPS: Detects and actively blocks threats in real time.



